Wanna Cry Patch Download Windows 7 Cnet Link
As a vicious new strain of ransomware swept the UK’s National Health Service yesterday, shutting off services at hospitals and clinics throughout the region, experts cautioned that the best protection was to download a patch Microsoft had issued in March. The only problem? A reported 90 percent of NHS trusts run at least one Windows XP device, an operating system Microsoft first introduced in 2001 and hasn't supported since 2014.
Windows 7 Home Premium won't download or install updates. Download and install KB3172605. Then visit this link to choose the package that is right.
NHS has disputed the 90 percent figure—though not that a significant portion of its systems run Windows XP—and was only one example of the tens of thousands of impacted computers across nearly 100 countries yesterday. But its meltdown illustrates the deeper problems inherent in Windows XP’s prevalence three years after its official demise.
Ransomware Everywhere
Experts rightly said that the best protection against the so-called WannaCry ransomware was to patch everything, as soon as possible. But for Windows XP and other expired operating systems, the patches weren’t there in the first place. With very few exceptions—including an emergency patch after the first wave of WannaCry infections and expensive, specialized service contracts—Microsoft no longer provides any security support for the OS. A computer running XP today is a castle with no moat, portcullis raised, doors flung open, greeting the ravaging hoards with wine spritzers and jam.
Wanna Cry Patch Download Windows 7 Cnet Link Download
And it’s only going to get worse.
Expiration Date
Hackers have targeted XP for years. Its lack of defenses and persistent popularity make it a popular target. And it really does have a foothold; according to analytics company StatCounter, 5.26 percent of Windows PCs run XP still, while a similar analysis from Net Applications puts the total at just over 7 percent of all personal computers. No matter whose numbers you use, that amounts to tens of millions of devices, and that’s before you count the absurd percentage of ATMs and other non-traditional systems stuck in the past.
Download Windows 7 Free
The natural question, given the absurd level of risk that comes with running Windows XP in 2017, is why on earth would anyone stick with it, much less millions of people and companies with so much to lose.
The problem stems in part from Windows XP's initial popularity. “It was one of the first Microsoft operating systems people latched onto,” says Peter Tsai, IT analyst at Spiceworks, a network for IT professionals. Not only was it one of the first stable Windows versions, the five-year gap between Windows XP and its unpopular successor, Windows Vista, resulted in an uncommonly large install base.
You can guess what happened from there; you’ve probably experienced yourself. Business-wide operating system updates take time and money, the kind that fall low on the priority list of a strapped CEO. “A lot of smaller companies subscribe to the theory, probably wrongly now, that if it’s not broken then don’t fix it,” says Tsai. “Especially companies that aren’t prioritizing IT.” Which appears to be most of them; a recent Spiceworks survey found than more than half of businesses worldwide have at least one machine running Windows XP.
Many companies have a more practical excuse than just lethargy; they may rely on specialized legacy software that simply won’t work with newer Windows releases. That may include institutions like NHS, where the process of testing new or updated versions of critical software could disrupt patient care.
But if nothing else, WannaCry makes clear that whatever time and money and disruption companies might think they’re saving by sticking with Windows XP is an illusion. If anything, in recent weeks the threats have only escalated.
New Tools
Download Windows 7 Iso
Last month, a group of hackers calling themselves Shadow Brokers released a set of purported NSA hacking tools on the internet. They included a previously undisclosed Microsoft vulnerability that targeted older versions of Windows. And it’s that exploit that WannaCry uses to wreak havoc.
This means a few things, none of them encouraging. First, that WannaCry is not a one-off event. There’s a whole suite of NSA tools now available to bad guys, whose interests may range from ransomware to targeted surveillance to building botnet armies and anything in between. Second, since those tools didn’t target Windows 10, any PC not running the latest Microsoft operating system finds itself at much greater risk than it did a month ago. Microsoft confirmed, in fact, that WannaCry didn't target Windows 10 at all.
By making a rare exception to its hands-off policy toward Windows XP, and issuing a patch that protects older systems (though doesn’t help PCs already infected), Microsoft undoubtedly helped slow the WannaCry spread. But that kind of selective, responsive patching won’t help the first wave of victims of the next big XP vulnerability. It also may give some XP laggards the impression that Microsoft will bail them out in the future, of which there’s no guarantee.
“It can give users a false sense of security, and does not motivate them to upgrade to systems whose security architecture is superior and can be improved on,” says Jérôme Segura, lead malware intelligence analyst at Malwarebytes.
Especially when so many active risks plague XP daily that don't rise to the level of WannaCry, but can still do harm. “If for some reason they are running Internet Explorer [on XP],” says Segura, “it would only take a few minutes of browsing the net before getting infected via malvertising or a compromised site.”
Maybe, then, the silver lining in WannaCry comes from alerting companies large and small of just how debilitating Windows XP can be. “A decade or two decades ago, most of these malware variants were pretty benign,” says Tsai. “Viruses were just a nuisance, instead of something that could impact the bottom line. But now with ransomware, where they’re encrypting or deleting your critical data, I think that the higher-ups who make decisions are starting to take note.”
If so, hopefully sooner than later. If you don’t want hackers taking shots at you, start by removing the bullseye.
This story has been updated to clarify that 90 percent of NHS trusts run at least one Windows XP system, rather than 90 percent of its systems on Windows XP.
Related Video
Security
What is Ransomware and How Do You Deal With It?
Ransomware. It's malware but worse. It takes the contents of your device hostage and demands Bitcoin as a, you guessed it, ransom. Here's how to avoid it and what to do if your laptop gets locked.
Microsoft just released a patch for Windows XP that fixes a file sharing flaw being exploited by the WannaCry ransomware. Here's how to install it.
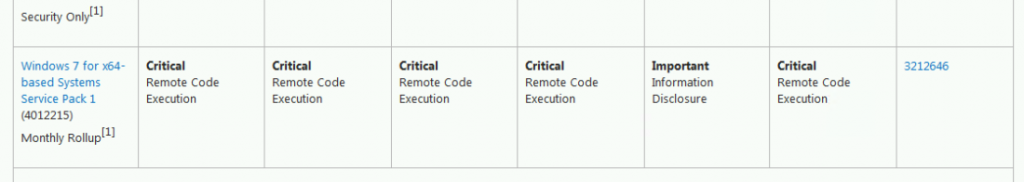
You can download some versions of the patch using links at the bottom of this May 12th Microsoft article: Customer Guidance for WannaCrypt attacks. The full list of patch variants, including languages other than English, is in the Windows Catalog, just search for KB4012598.
For an x86 machine with Service Pack 3 installed, the downloaded file name is
windowsxp-kb4012598-x86-custom-enu_eceb7d5023bbb23c0dc633e46b9c2f14fa6ee9dd.exe
I know, its looks like malware itself. The file is small, only 665K. Logon as an Administrator and, for good luck, make a Restore Point first thing.
To see if System Restore is enabled, right click on My Computer, get the Properties and go to the System Restore tab. To actually make the Restore Point, go to Start -> Programs -> Accessories -> System Tools -> System Restore.
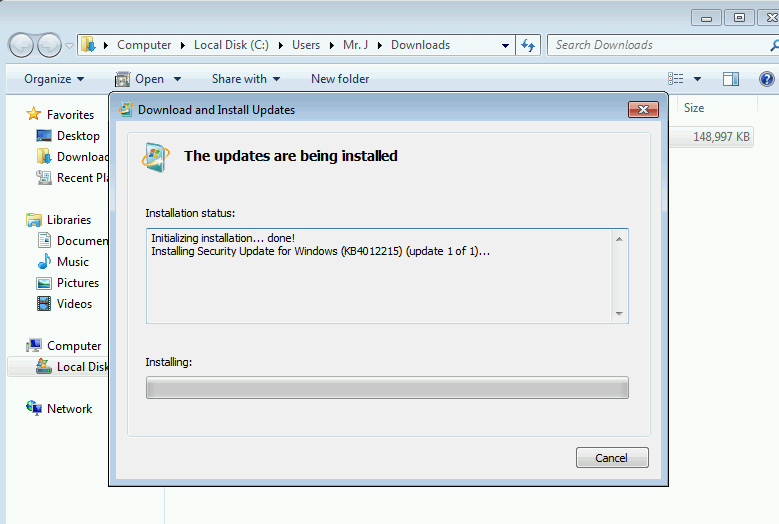
The installation process is simple.
1. Wizard warns you to backup your system and close all open programs
2. Then you have to agree to a license
3. Installing the patch takes only a few seconds, even on old hardware. It first asks you to wait while it 'inspects your current configuration, archives your current files and updates your files.' Then it makes a restore point.
4. When its all done, it wants you to reboot
Ms17-010 Patch Download Windows 7
After rebooting, you can verify that the patch was correctly installed using Add or Remove Programs in the Control Panel. You first need to turn on the checkbox to 'Show updates.' Then scroll down looking for the 'Windows XP - Software updates' section. It should be huge.
In this section, look for 'Security Update for Windows XP (KB4012598)' with the current date as the date installed (see above). Considering this is Windows XP, the installation date should stick out like a sore thumb. On two machines that I tested, it was, fortunately, the last entry in the list.
The fix applies to the file sharing component of Windows (Server Message Block or SMB) and thus prevents an XP machine from being infected over a LAN (Local Area Network). However, it would not protect an XP machine that was attacked another way, via email, for example.
I checked around (here and here) and Microsoft has not issued an update to their free anti-malware software, Security Essentials, for Windows XP. When XP went off support, it was denied access to Security Essentials. Thus, XP machines remain vulnerable to WannaCry, just not via file sharing on a LAN.
Download Windows 10
To fully protect an XP machine requires a third party antivirus product. Lotsa luck with that.
BitDefender bragged today that they can protect against WannaCry, but they do not support Windows XP (see below for update). Neither does Avira, Trend Micro or F-Secure. Kaspersky still supports XP, but their website says nothing about WannaCry.
So, yes, Microsoft released a patch for Windows XP. But now you know the rest of the story.
UPDATE: May 15, 2017. A reader was nice enough to point out that Bitdefender does offer a product that supports Windows XP (and Vista too). The name is fairly direct: Security for XP and Vista.
UPDATE: May 15, 2017. A couple people have told me that when they verified the installation of the patch, the install date was not the current date but tomorrows date. Beats me why.
FEEDBACK
Get in touch with me privately by email at my full name at Gmail. Public comments can be directed to me on twitter at @defensivecomput